- +61 7 3374 2877
- Email Us
Global industrial connectivity supplier Moxa, distributed in Australia by Madison Technologies, introduces the defense-in-depth concept that allows businesses to leverage their existing network infrastructure and investment to build the first line of their network defense.
The rise of interconnected OT and IT systems is often attributed to how business models have evolved with the purpose of enhancing operational efficiency. For example, SCADA networks deployed along oil pipelines now collect oil output data that is essential to billing and pricing systems.
This increase in data collection allows companies to predict with higher levels of accuracy not only levels of oil production and output, but also expected revenue. However, it should be noted that these interconnected systems do not only bring benefits. A downside of these systems is that the likelihood of introducing cybersecurity threats to OT systems increases significantly. It is for this reason that newspaper headlines and articles often describe how the compromising of IT systems can have a hugely negative impact on OT systems. What is compounding this complex issue even further is that ransomware attacks are increasing in their severity. This type of malware exploits Windows vulnerabilities and attacks insufficiently protected systems.
With more and more similar cybersecurity incidents occurring in OT systems, business owners and regulators are keen to seek solutions that enhance industrial cybersecurity and allow businesses to keep functioning normally.
What Is the Security Boundary Concept?
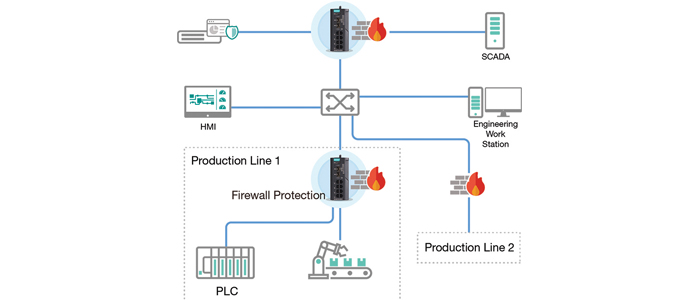
When enhancing cybersecurity, it is important to understand how your industrial systems are exchanging data within different systems and how they connect to IT-level systems. In the most ideal scenario, when traffic crosses different systems, there should be boundaries in place between each system to ensure the traffic has good cyber-hygiene, even if it is authenticated and authorised. However, it is challenging, and often unrealistic to build boundaries between every system, as it involves significant expenditure, and often has a detrimental effect to the efficiency of network communications. It is for these reasons that it is highly recommended to divide OT systems into different digital cells and zones and build up the boundaries to find the right balance between expenditure and acceptable levels of risk.
The defense-in-depth approach, which is recommended by the IEC 62443 cybersecurity standard committee, is widely used across industries, and has a good track record of helping build up multiple layers of protection to fulfill operational requirements. In the picture below, the critical assets and operations are considered the most important. As they perform vital roles for businesses, it is wise to take additional security precautions, such as adding more layers of protection, to secure them further.