- +61 7 3374 2877
- Email Us
Global industrial connectivity supplier Moxa, distributed in Australia by Madison Technologies, explores the importance of proactively protecting your industrial networks.
In recent years, increased cybersecurity incidents have been crippling critical infrastructure and harming businesses. Some are targeted attacks, such as ransomware attacks; however, some are non-targeted incidents, such as contamination through malware that gains access to an unauthorised computer and spreads to the whole industrial control network. Taking the approach of creating zone-basis industrial network architecture can reduce the damage. In the meantime, cybersecurity experts are also proposing more proactive actions to protect industrial networks. These actions can be realised by an industrial intrusion prevention system (IPS), which can effectively counteract intrusions and reduce their impacts on industrial systems.
What is an IPS?
An IPS is a form of network security designed to detect and block identified threats by constantly monitoring networks, looking for possible malicious cyber-incidents and logging information about them. It features deep packet inspection (DPI) technology, enhancing network security visibility, and ultimately helps mitigate risks and protect industrial networks from security threats.
Industrial IPS Tailored for Industrial Networks
Although IPS technology has worked very well on IT networks for a while, it is difficult to directly deploy an IPS in OT networks because the first priority of OT networks is availability and performance, while the first priority of IT cybersecurity is confidentiality.
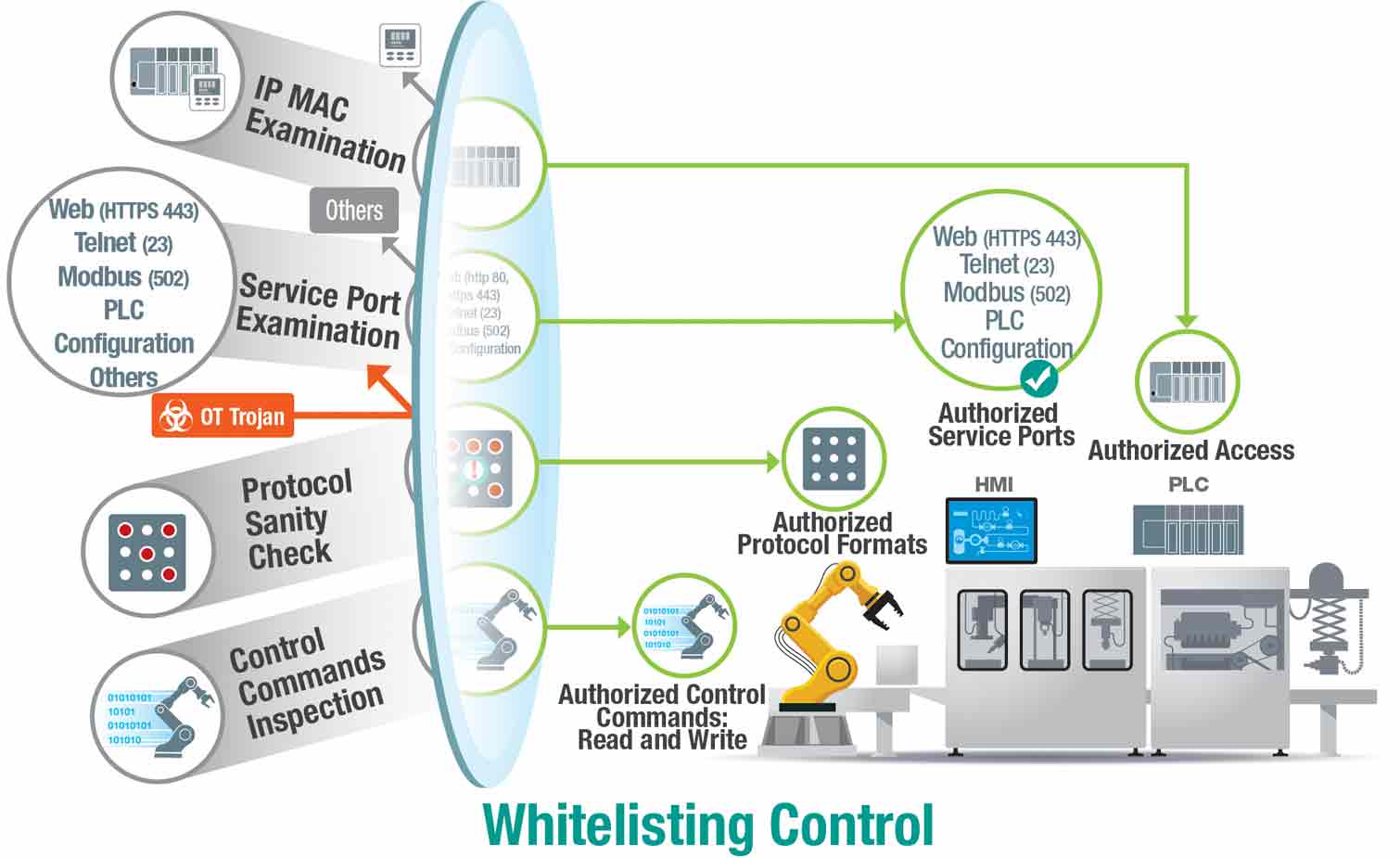
Implementing an IPS in OT networks without considering the daily operations requirements of OT engineers could possibly block control commands that are important to production, consequently disrupting operations. To fulfill the OT cybersecurity requirements, it is essential to empower OT-centric DPI technology. OT-centric DPI can identify multiple industrial protocols and allow or block specific functions, such as read or write access. Based on the identified protocol, an industrial IPS can then prevent any unauthorised protocols or functions. This ensures that the traffic on industrial networks is trusted and non-malicious.