- +61 7 3374 2877
- Email Us
Within critical infrastructure, electrical substations are entrusted with the vital role of ensuring the dependable delivery of electricity to homes and industries. These modern substations, powered by digital technologies, lean on the IEC 61850 communication networks for orchestrating seamless interoperability and integrating a diverse array of devices and functions.
While digital transformation undeniably bolsters operational efficiency and effectiveness, it simultaneously unlocks the door to a new breed of cyber threats, each capable of jeopardising the very operation and safety of these indispensable facilities.
In response to the evolving threat landscape, the imperative for a novel cybersecurity approach tailored to the intricacies of IEC 61850 communication networks becomes abundantly clear. This innovative strategy is epitomised by functional security monitoring, a vigilant practice revolving around the continuous scrutiny of the operational health of critical systems and devices nestled within substations. Through this continuous monitoring, any aberrations or anomalies are promptly identified, empowering swift action to curtail the ascent of potential cyber threats employing tricks such as Ethernet ghosting.
What is Ethernet ghosting?
Ethernet ghosting represents an elusive cyber threat that poses a grave danger to OT power utilities. In traditional methods of network infiltration, attackers typically leave traces identifiable through their MAC (Media Access Control) and IP addresses. When a network is equipped with a properly configured detection system, it triggers alerts upon detecting these intruders. However, to circumvent detection, attackers resort to Ethernet ghosting.
Ethernet ghosting is a method employed by cyber attackers to connect their device to a network undetected. They achieve this by sending messages using the MAC address and physical Ethernet connection of a legitimate device already on the network. Effectively, the attacker’s device cloaks its communication by merging it with legitimate traffic over a shared physical connection. From the perspective of the switch and the network, there appears to be only one device transmitting packets on behalf of a single MAC address.
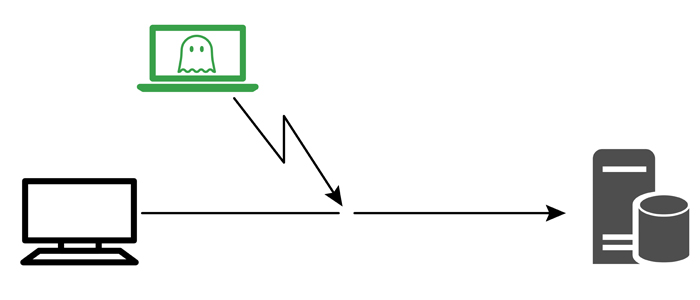
The mechanics of an ethernet ghosting attack
So, how do Ethernet ghosting attacks actually work? Let’s break down the process: